AWS Bastion AMI User Guide

In the wild world of cloud stuff, there's this cool thing called a Bastion Host that not many people talk about. But hey, it's like the secret agent of Amazon Web Services (AWS), silently keeping things safe and sound. So, what's the deal with this Bastion Host, you ask? Well, it's like the front door to your AWS world. You know, the bouncer that decides who gets in and who doesn't. In this guide, we're going to spill the beans on what a Bastion Host is, why it matters, how to use it with our AMI and how it's basically the unsung hero of securing your AWS stuff. Whether you're a tech whiz or just dipping your toes into the AWS pool, come hang out with us as we break down the Bastion Host. Let's uncover its secrets, figure out why it's a big deal for keeping your cloud stuff safe, and get a grip on this whole AWS security thing. Get ready to level up your cloud game and become the master of your AWS domain!
What do we offer with our Bastion AMI?
1. Security Best Practices
Our AWS Bastion AMI is configured with security best practices in mind. As minimum AMI includes recommended settings and configurations required by AWS, reducing the risk of overlooking crucial security measures. Additionally it includes pre-configured firewall rules, ensuring that only essential communication is allowed. The operating system settings are hardened to reduce the attack surface, and unnecessary services or ports are disabled to minimize potential entry points for malicious actors. Our approach significantly reduces the likelihood of overlooking critical security configurations that might be missed when setting up a Bastion Host manually. Moreover, our Bastion AMIs incorporate the latest security updates and patches, providing a solid foundation that aligns with current security standards.
2. Time and Effort Savings
Building a secure and functional Bastion Host from scratch involves various steps, including configuring the operating system, setting up security measures, and fine-tuning access controls. This process demands a significant investment of time and technical expertise. Choosing our Bastion AMI streamlines this journey, resulting in substantial time and effort savings. This is particularly beneficial in scenarios where rapid deployment is crucial, such as during sudden increases in workload or in response to dynamic operational requirements. Our Bastion AMI is for users who might be less experienced in AWS or those who prioritize efficiency in their deployment workflows. Instead of investing hours or days in setting up a Bastion Host, you can launch instances based on a pre-made AMI within minutes, allowing you to focus on other aspects of cloud infrastructure.
3. Consistency Across Environment
Prezelfy Bastion AMI provide consistency across different environments. Whether you're setting up multiple Bastion Hosts for different projects or replicating your infrastructure in various regions, using the same pre-configured AMI ensures uniformity. This helps in maintaining a standardized and easily manageable infrastructure. Bastion AMI is replicated automatically through multiple AWS regions.
4. Version Control and Updates
Bastion AMI is versioned, allowing you to keep track of changes and updates. When security patches or improvements become available, the AMI is updated, and instances can be launched with the latest version. This ensures that your Bastion Hosts are running on the most secure and up-to-date configurations. All versions are documented on our GitHub repository.
5. Documentation
Our AMI comes with documentation that guides you through common configurations and troubleshooting steps. This not only accelerates the deployment process but also aids in ongoing management, reducing the time spent on maintenance and support.
Architectural design
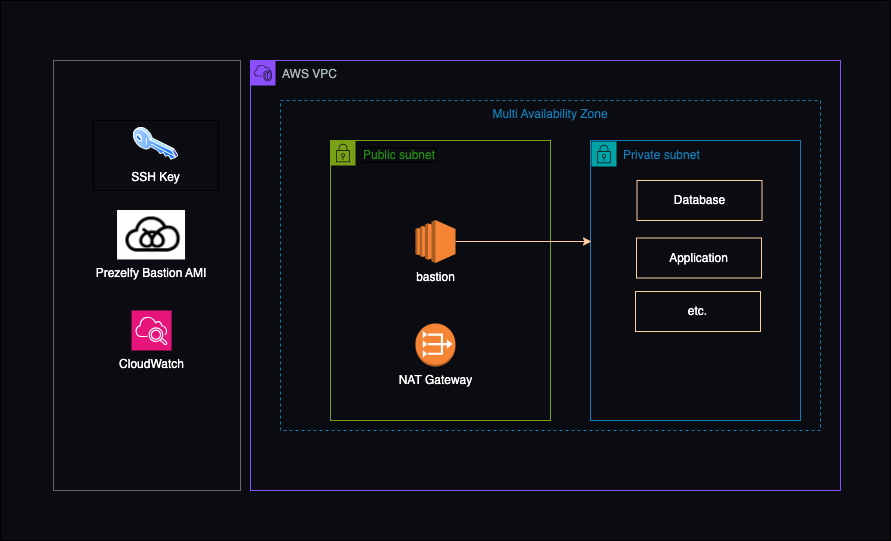
The bastion host is usually a single EC2 instance deployed in a public subnet within an VPC. The instance is configured with a minimal set of security group rules to allow incoming SSH traffic, depending on the operating system, from specific IP addresses or IP ranges. Bastion is in public subnet which allows the bastion host to have a public IP address and be reachable from the internet, but other instances in private subnets are not directly accessible from the internet. Instances that need to be accessed (e.g., application servers, databases) are deployed in private subnets and they not have a direct route to the internet, providing an additional layer of security for internal resources. Ingress rules on the bastion host's security group allow SSH or RDP traffic, while egress rules allow necessary outbound traffic. Access to the bastion host is typically secured using key pair authentication. Users must possess the private key associated with the key pair to connect to the bastion host securely.
Installation guide
Installation steps assuming you have already configured the VPC:
- Create single EC2 instance, or one using Auto Scaling group
- For AMI ID select one assigned to Prezelfy Bastion AMI
- Generate key pair and save private key on secure place
- Deploy
- Share bastion public IP and private key with your team
Installain steps if you didn't configure VPC:
- Follow steps from AWS guide
- For AMI ID select one assigned to Prezelfy Bastion AMI
- Share bastion public IP and private key with your team
How to use Bastion?
Bastions serve various purposes, and we'll highlight a few of them here. Utilizing bastions aligns best with company security standards and company security team.
Use usecases:
1. Secure Remote Access
username: ec2-user
password: use SSH-key used during EC2 instance creation
Example:
ssh -i /Users/Prezelfy/Keys/bastion.pem ec2-user@prezelfy-bastion.com
ssh -i /Users/Prezelfy/Keys/bastion.pem ec2-user@prezelfy-bastion.com
2. Local Secure Database Access
ssh -i path-to-private-key -L LOCAL_PORT:DESTINATION-DB-HOSTNAME:DESTINATION_PORT user@bastion-hostname
Example:
ssh -i /Users/Prezelfy/Keys/bastion.pem -L 5432:prezelfydb.local:5432 db-admin@prezelfy-bastion.com
3. Cross-Account Access
Using a bastion host for cross-account access involves setting up a secure intermediary server that acts as a gateway between different AWS accounts. This is particularly common in AWS environments where you have multiple accounts and need controlled access between them. Here's a general guide on how to set up a bastion host for cross-account access:
- Create IAM Role for Cross-Account Access
- Establish a trust relationship in Bastion Host by Attaching a policy to this role that allows Bastion instance to assume roles
- SSH into bastion, as showed in Use case 1.
- Assume the IAM role using aws sts command
aws sts assume-role --role-arn arn:aws:iam::TARGET-ACCOUNT-ID:role/RoleName --role-session-name CrossAccountSession
4. Secure File Transfer
ssh -i path-to-private-key -L LOCAL_PORT:DESTINATION-HOSTNAME:DESTINATION_PORT user@bastion-hostname
Example:
ssh -i /Users/Prezelfy/Keys/bastion.pem -L 3333:prezelfyserver.local:4444 server-admin@prezelfy-bastion.com
On Local Machine use SFTP as intended:
sftp 127.0.0.1:3333
Troubleshooting when Bastion is not working
This are some of the cations we recommended to take when Bastion host is not functioning as intended:
1. Check Network Connectivity
Ensure that the bastion host has a public IP address or an Elastic IP, confirm that the security group associated with the bastion allows inbound SSH traffic from your IP address and verify that there are no network ACLs or route table rules blocking the traffic.
2. Verify Bastion Instance Status
Check the status of the bastion host instance. If it's terminated, you may need to relaunch it.
3. Inspect Security Group Rules
Confirm that the security group associated with the bastion allows outbound traffic to the target instances, ensure that the security group rules for the target instances allow inbound SSH traffic from the bastion host.
4. SSH Key Pair and Permissions
Verify that you are using the correct SSH key pair to connect to the bastion host and check the permissions on the private key file (it should only be readable by the owner).
5. EC2 Instance Metadata
On the bastion host, check the EC2 instance metadata for errors or issues. Access metadata at http://169.254.169.254/latest/meta-data/ on the bastion host.
6. IAM Role Trust Relationships
Review the trust relationship policy attached to the IAM role in the target account, Ensure that it allows the bastion account to assume the role and check if the IAM role in the target account is still valid and has not been modified.